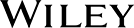USA
800 691 9120
UK
01225 704844
We use cookies on our website to analyze website usage and to help secure the website against misuse. Advertising and functional cookies are not used in our site or our web application products.
By clicking “Accept Essential Cookies Only”, you consent to us placing these cookies.
A cybersecurity assessment helps verify that your organization follows best practices. An Asset Management System (AMS) can make this process faster and more effective.
By discovering, tracking, monitoring, and reporting on business assets, AMS tools like xAssets ITAM offer features to assess endpoint and network infrastructure, delivering insights in seconds and expediting the cybersecurity assessment process.
Effective risk management is vital in keeping your network secure. AMS can help in identifying and minimizing the risk of vulnerabilities, by identifying them before they can be exploited. Effective assessments typically evaluate at least the following:
The first step of a cybersecurity assessment is to identify the questions which can be completed using asset management software. Typically, these will include questions from many categories of the assessment such as the Scope of assessment, Firewall and Internet access, Device Configuration and Management, Operating systems and Software updates, User accounts and authentication, and Malware protection. Planning which areas and specific questions can be addressed with AMS will save you time and resources, simplifying the process.
Security assessments can be time consuming, and sometimes frustrating. Therefore it makes sense to have an ITAM system do some of the work for you. We've used several toolsets where you can type a long answer, and then get logged out before you had a chance to save it, or you find yourself answering the same question in different sections. One point of frustration we recently discussed with a customer was for server logins, each user had to have a non administrative login, and an administrator account. This requirement effectively doubles the number of accounts, which in itself introduces a security risk, yet the customer was not permitted to pass the audit without this.
Given these frustrations, we suggest this approach to audits:
The scope of the assessment will determine focus areas and boundaries of the evaluation.
Defining the scope requires identifying the systems, processes, and assets to include, and some parts of your organization might need to be excluded. An AMS like xAssets ITAM offers a platform with your asset data all in one place, allowing for easy identification of components and systems within your company which should be included in the assessment.
Additionally, you should specify out-of-scope areas to clarify the bounds of the assessment, to avoid spending time, effort, and technical resources on areas irrelevant to the objective of the assessment. This ensures that the use of AMS is directed to where it is most appropriate, while alternative assessment methods can be identified for aspects in which AMS isn't appropriate.
Examples of systems which are excluded from the scope might include:
Test environments often need to run old versions of OS's and other software to be able to prove that a software bug is fixed. Cybersecurity audits will usually require that these networks are isolated from the other networks.
Letting BYOD / personal devices onto your network will always be a security risk, therefore you should have a BYOD policy in place.
Work from home networks (WFH) need to be secure. This means your employees home routers should have strong passwords and firewalls enabled with no incoming ports allowed. Devices within these networks should be running automatic updates. Devices with work data on should be owned by the company, and should be managed and secured under your ITAM or MDM systems
In these instances, it is the duty of the IT team to discover and normalize this data.
Example information which you will be required to supply for a comprehensive cybersecurity assessment relating to the scope of your assessment:
Firewalls are often the first line of defense against cyber threats, preventing both incoming and outgoing network traffic based on a configurable set of rules. Typical questions you might find relating to firewalls and internet access in a cybersecurity assessment include:
Most audits will mark network devices as non-compliant if they are no longer supported by the manufacturer.
Using an AMS allows for:
If you use Windows Firewall, xAssets can list computers by firewall rule in a query:
xAssets Network Discovery also discovers SNMP based equipment including firewalls, the data collected includes the OS and patch level, and the system is configurable and extensible so you can discover any MIB/OID. This data is placed inside the asset register in the AMS, alongside other endpoints like PCs and Servers.
Device management and health is essential for keeping your business safe from cyber attacks. Devices running old or unsupported software, or devices with poor configuration render cybersecurity efforts in other aspects of your network a liability. To ensure a robust approach, each device should have only the necessary software and services enabled, and frequent user account and privilege checks.
Key questions on device management and configuration:
With the discovery power of an AMS, these tasks can be simplified by the generation of detailed reports and identification of devices across your network with information about installed software, running services and user accounts.
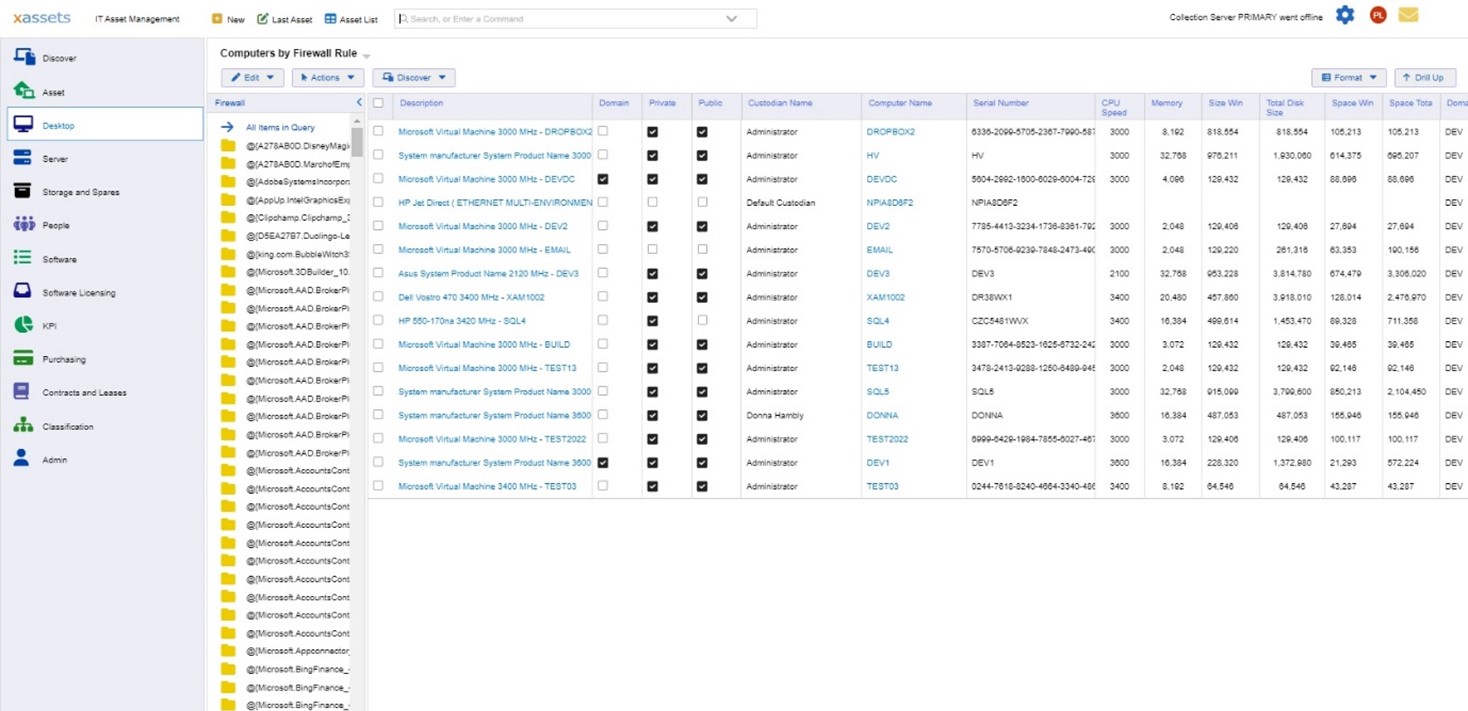
This screenshot from xAssets shows the installed software on a desktop computer, with versions on the right side:
AMS can help in improving the physical security of your IT assets. Since AMS provides a central repository to accurately track device locations, the risk of losing an asset is reduced, especially if you use discovery tools which update location from IP address. This is particularly important for endpoints like laptops and mobile devices of employees, in a business which has a number of remote workers for example. xAssets can create administrative user account and other user group rights, so that only the required information can be accessed by certain users.
Windows desktop devices should typically be updated every Tuesday, whereas it is often preferable to update servers on weekends or overnight to minimise interruptions to users. These procedures and processes should be documented in your security guides. It is common for Windows desktops to be updated automatically and this can be set in Group Policy.
Data stored on laptops, tablets, and other mobile devices often poses the greatest risk of compromise due to their portability and exposure outside secure office environments. While on-premises devices like desktops and servers should also be encrypted, the 80/20 rule suggests prioritizing mobile devices, where the majority of data breach risks originate.
For organizations worldwide, most laptops run Windows, offering a head start on security through built-in encryption tools. Enabling BitLocker—a full-disk encryption feature—during Windows installation, paired with a Trusted Platform Module (TPM) chip, provides a robust foundation for protecting data at rest. TPM enhances security by securely storing encryption keys, ensuring that data remains inaccessible if a device is lost or stolen. An Asset Management System (AMS) like xAssets ITAM simplifies encryption management by discovering and reporting on encryption status across your network. Its discovery tool detects whether BitLocker is active on Windows devices, flagging any unprotected endpoints for immediate action. This visibility is critical during a cybersecurity assessment, as auditors often require evidence of encryption compliance, especially for mobile and remote devices. Key questions to consider for device encryption in a cybersecurity assessment include:
The discovery tool within xAssets ITAM includes detection of Bitlocker, and the same data can also be accessed via Intune and SCCM integrations.
Regular and secure backups are a critical component of any cybersecurity strategy. They ensure that data can be recovered in the event of data loss, corruption, or a cyber attack such as ransomware. Properly managed backups can significantly reduce downtime and data loss.
Key questions to consider for backup management in a cybersecurity assessment include:
To ensure all data is protected, backups should be organized as follows:
Utilizing an AMS can help streamline the backup process by providing detailed reports on backup status, storage locations, and retention policies. This ensures compliance with security policies and provides a clear audit trail for security assessments.
Managing user access is crucial for maintaining the security of your IT environment. Ensuring that only authorized personnel have access to sensitive information and critical systems helps mitigate the risk of data breaches and unauthorized activities.
Key questions to consider for user access management include:
Utilizing an AMS can streamline the management of user access by providing detailed reports on user accounts, access levels, and activity logs. This helps ensure compliance with security policies and provides a clear audit trail for security assessments.
AMS reports on software versions, so a comparison of versions of each title across different devices will help determine which devices have the latest version.
SAAS software should be protected by a "Single Sign On" (SSO) security wall. This usually includes Multi-Factor Authentication (MFA). Many products including xAssets support SSO from providers like Microsoft Entra ID, Duo, Okta, Onelogin, etc.
Low disk space poses a security risk and can become problematic once it begins to impair a system's ability to function, making the system susceptible to malware attacks. This can occur when critical security processes are unable to run as normal due to crashing and other issues. These could include:
Therefore ensuring devices have enough disk space to function is not only important for availability, but also for security.
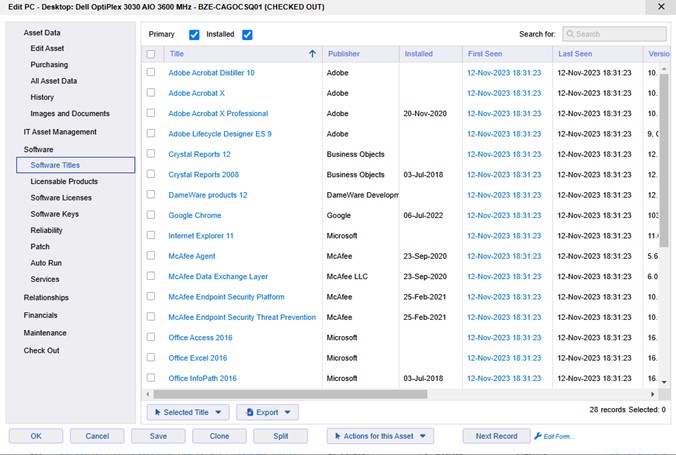
xAssets provides a built in tool to show which devices are low on disk space. They can be sorted by allowing technicians to prioritize freeing up space or reconfiguring the most important devices first.
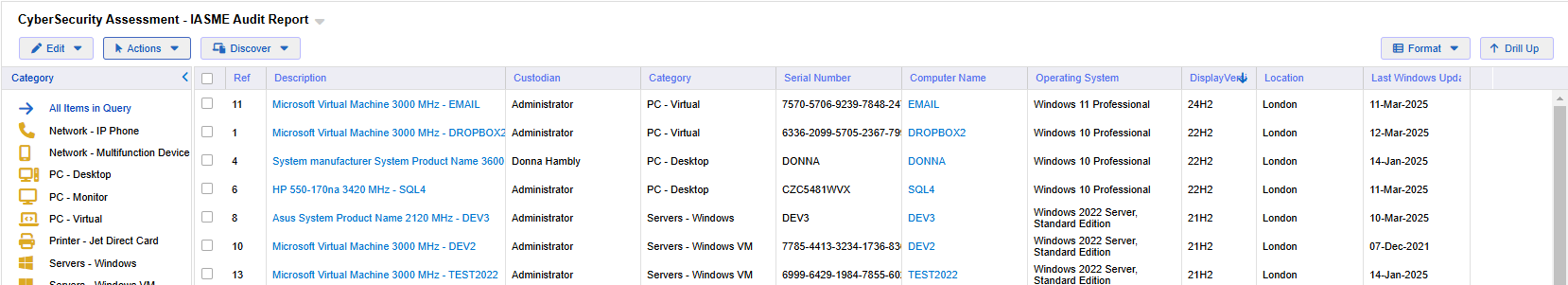
Creating reports within your AMS should be quick and easy. Below is a report from the xAssets system for IASME CyberSecurity Audits, showing the "Windows Display Version" field which is required in these assessments:
As covered earlier in this document, AMS can be an extremely helpful tool in conducting cybersecurity assessments, saving you both time and money, whilst ensuring higher accuracy than manual methods. By automating collection, organizing, and reporting of asset data, the process for evaluating compliance with specific frameworks such as GDPR, SOC 1, SOC 2, HIPAA, and FedRAMP is made simple.
Here are some examples of specific security frameworks and how xAssets can help achieve their requirements:
| Compliance Standard | Description |
|---|---|
| SOC 2 | AMS can help to answer security questions by providing an inventory of user accounts, highlighting encryption compliance, for example, in the usage of BitLocker. |
| ISO 27001 | Having a centralized asset inventory aids in assessments for the ISO 27001 framework, enabling businesses to track assets with high accuracy, ensuring all endpoints, software, and network components are accounted for during the evaluation process. |
| FedRAMP | AMS can assist with the requirement for documenting and monitoring the use of cloud services. Continuous tracking of asset configurations ensures compliance, e.g., incident response, and data encryption both at rest and in transit. |
| SOC 1 | AMS can provide audit-ready reports and documentation of system changes, user permissions, and access logs, ensuring only authorized users have access to protected financial data. |
| GDPR | The mapping of data flows with an AMS tool allows businesses to identify where personal data is stored and to document measures for access control. Report generation can also be helpful in demonstrating compliance with specific requirements including data minimization and retention. |
| HIPAA | Healthcare relies heavily on AMS due to its ability to provide detailed records on both fixed and IT assets used to send, store, or process protected health and patient information. |
Protecting your data is more important than ever, and taking a cybersecurity assessment is a great way to make sure your network is protected. Asset management Software can make the process more efficient, saving you time and money. Tools like xAssets streamline assessments, helping you build a more secure IT environment. xAssets makes it simple to track your assets and to identify security weaknesses, allowing you to ensure compliance with security frameworks. Its powerful features like endpoint discovery, firewall rule discovery, reporting, and integrations, help you to stay on top of your security.
Free instances are free forever and can show demo data or your data.